How to Manage Endpoint Security for Your Remote Workers
Index Of The Blog
In recent years we have seen the rise of digital technology and a monumental increase in the usage of smart computing devices. Businesses across the globe and even private entities have become heavily reliant on managing their business operations with the help of technology.
This, in some part, is the reason why cybercriminals have directed their attacks at huge corporations dealing with volatile and sensitive information. Hence endpoint security is fundamentally essential more than ever to manage loopholes and entry points into a private network.
According to a recent study by Help Net Security, 68% of IT security professionals reported an endpoint attack that compromised data assets and infrastructure in 2019. Furthermore, 80% of attacks were found to be new and unknown, thus labeled as ‘zero-day attacks’.
The average cost of an endpoint breach was found to be around $9 million in 2019. Moreover, 80% of organizations have been reported to upgrade their systems and move away from legacy antivirus solutions which are outdated and ill-equipped to combat present-day threats.
In light of this information, let’s take a quick look at some of the ways through which you can manage endpoint security for remote workers.
1. All-Encompassing Data Policy
What are the criminal minded and people with malicious intent after? It’s the data which is volatile, private, and contains sensitive information. Hence probably the first thing that any organization needs to do is to create an all-encompassing data privacy policy.
This will ensure that each person in the organization is made aware regarding how to protect data and use data following best practices.
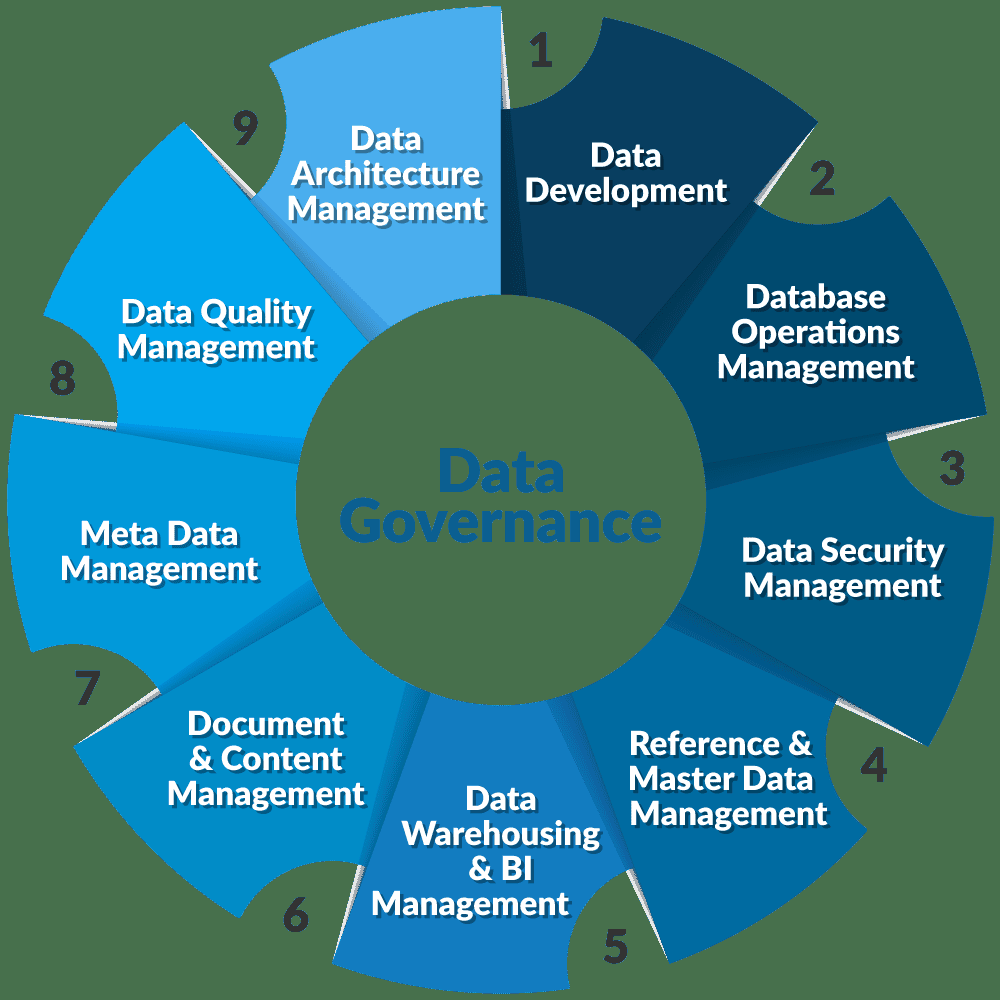
This can directly fall under your greater ‘Data Governance Policy’ which offers employees guidelines regarding the management of data and organization’s private information.
If your company doesn’t have a comprehensively designed data policy, now is a good time as any to develop and implement it at all levels of your organization, including remote workers.
2. Build Awareness for Threats

We are living in a world that has become increasingly interconnected through the use of technology. This is why all of our employees, stakeholders, and even clients should be made aware of cybercriminal activities and the threats which they impose, including remote workers.
To build awareness, you can follow up with training and professional development of workers to manage their actions in a way that are deemed necessary to avoid data leaks as well as protect themselves whenever using technological devices at their workstations.
This will help them understand the alarming consequences of data breaches. It is important that you teach them about cyber-attacks and also implements regulations that can hold people responsible for careless acts that can compromise the integrity of your organization.
3. Consistent Threat Evaluations
As a business owner or IT manager, it is your prime duty to ensure that all threats are evaluated constantly and consistently. In order to do this, you need to come up with a periodic assessment cycle that intervenes business operations to cross-check every possible loophole within a system or network.
You need to deploy a monitoring tool to check the infrastructure as well to make sure that endpoint security is properly maintained even for remote workers. Here are some measures that you can take:
- Invest in SIEMs or security information and event management platforms for better visibility & control.
- Deploy a SOAR (security, orchestration, automation, and response) system that allows your team to respond to threats swiftly and effectively.
- Join the MITRE and ATT&CK frameworks that offer comprehensive and globally accessible knowledge about attackers, tactics, and techniques based on real-world observations.
4. Cybersecurity EDR
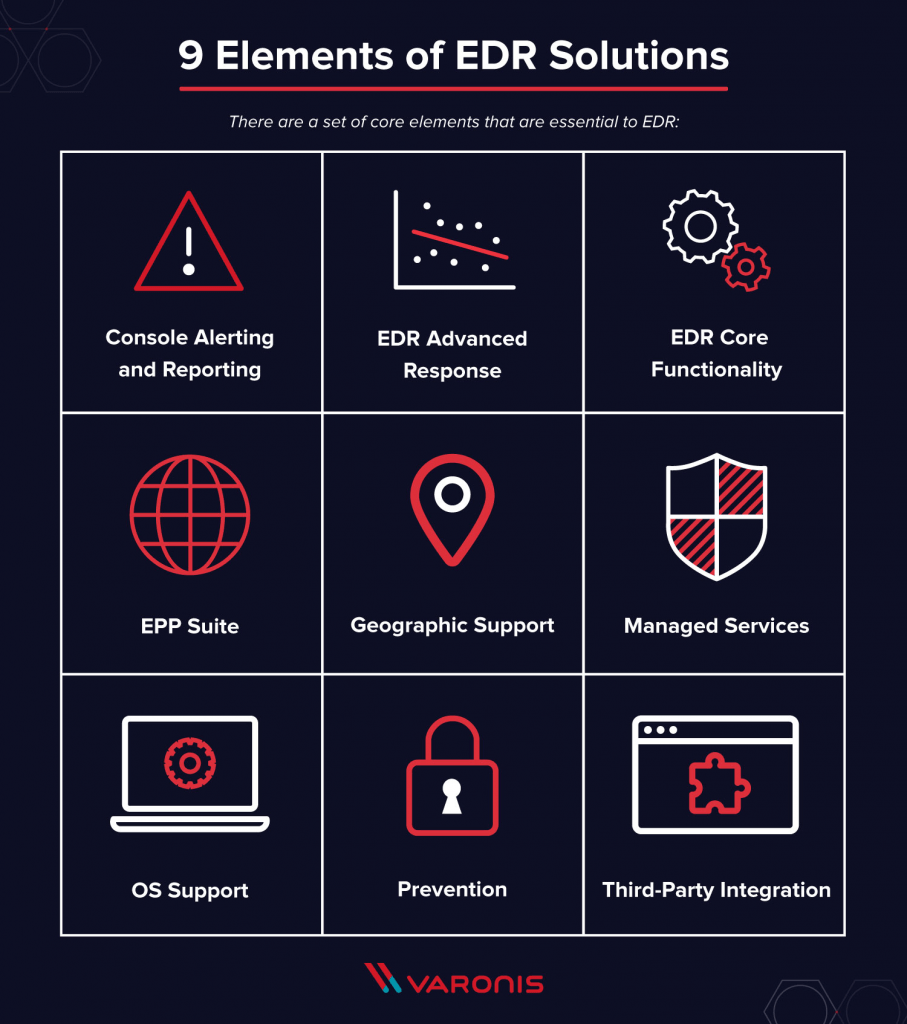
Endpoint detection & response or EDR is also known as ETDR (endpoint threat detection and response). It is a security solution that combines continuous real-time monitoring as well as the relay of endpoint data with a rule-based automated response system with complete analysis capabilities. The primary functions of EDR security systems include:
- Analyze data patterns and identify threats by evaluating system arrays and configurations.
- Collecting and monitoring activity data from all endpoints that could point towards a threat.
- Notify security personnel regarding any anomalies in the system when they are detected.
- Respond automatically to threats when they are identified and remove or contain them.
- Search for suspicious activities and utilize analysis and forensic tools to research threats.
5. Endpoint Protection Software

Endpoint protection software is specifically designed to keep entry points to a private or company-owned network secure from breaches or outside penetrations.
It offers protection for end-user devices, including desktops, laptops, and smartphones from being manipulated and exploited by cybercriminals. Some of the best endpoint protection software includes:
- Avast Endpoint Protection for Small Businesses
- Bitdefender Gravityzone Security for Endpoints
- Crowdstrike Falcon Endpoint Protection
- McAfee Endpoint Security
6. Monitor User Activity
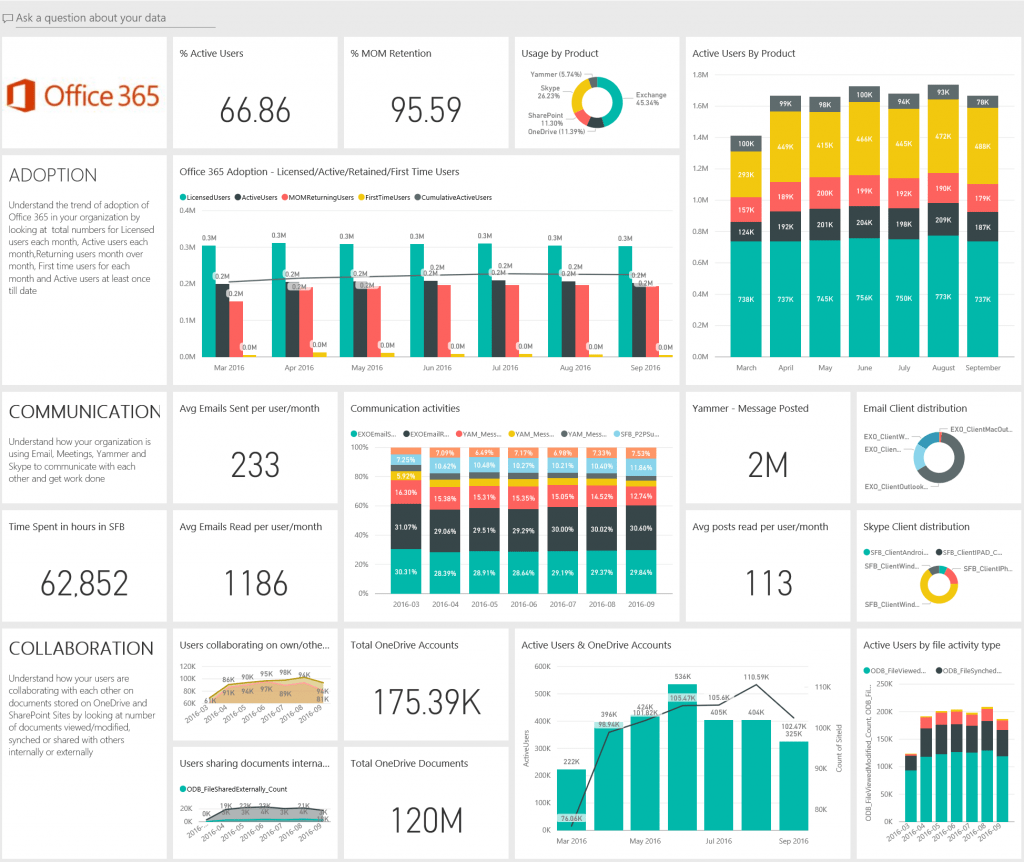
There is a list of software available in the market that can help you monitor the activities of your employees, including remote workers.
They offer you detailed information regarding their on-screen time, use of applications, time allocated and invested into documents, file sharing, and even snapshots of their screens every 5 seconds.
As a manager you are provided with a detailed dashboard with insights as to how your workers are performing and how they are allocating their time in accordance with their designated task, their use of the internet, websites visited, and much more.
Some of the best software for monitoring employees includes the likes of:
- ActivTrak – free software for employee monitoring
- Hubstaff – best for maintaining productivity
- SentryPC – ideal for monitoring small business activities
- Teramind – overall top of the pick for employee monitoring
- Time Doctor – the perfect choice for remote teams and businesses
7. Multifactor Authentication
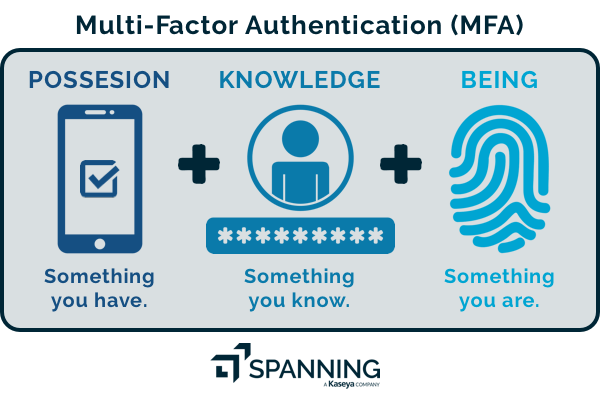
Image Credits
Another way to augment endpoint security is to provide multifactor authentication for your remote employees. This would require them to access data by entering a variety of security combinations, thus making it difficult for outside parties to get through your system’s security and get access to private networks. Multifactor authentication can be applied for a wide variety of smart computing devices.
However, it is best that whatever device is being used by your remote employee; they are registered and reported to your IT managers and security advisers. This will allow them to intervene if any abnormal or unwanted activity is observed through those devices. Many students these days who require essay help are also observed using 2-factor authentication to gain access to online academic resources and perform research for their subjects and topics.
8. Prepare & Maintain Backups
This is probably the last precaution and the least that you can take to protect your data from being lost through remote workers and their activities. Data backups are essential since, during an event of a breach, they can help your systems and networks to recover.
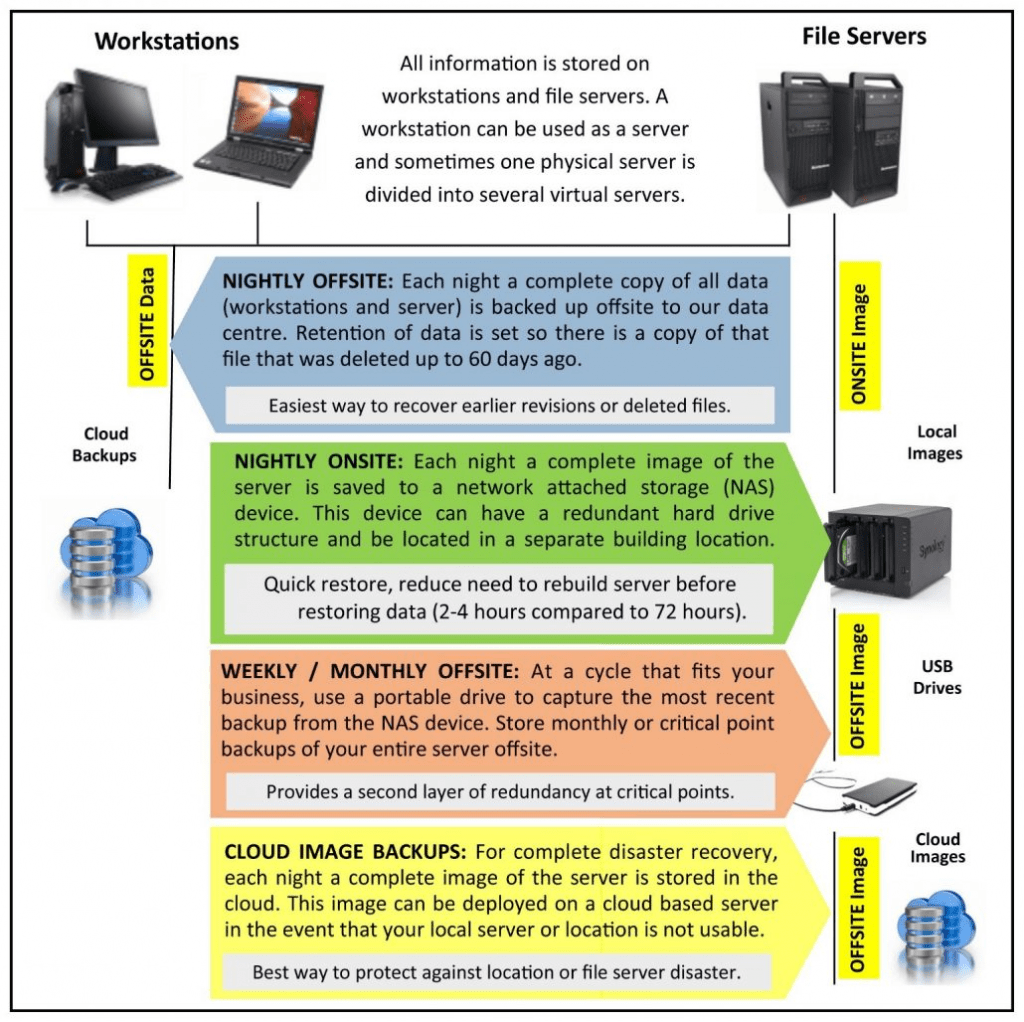
This allows your company to maintain operations while simultaneously deploy resources to fight back threats in real-time. However, data back strategies are best when they are practiced in secrecy, and all data backups are thoroughly and routinely checked to maintain the integrity of your systems.
9. Up to Date Devices & Networks
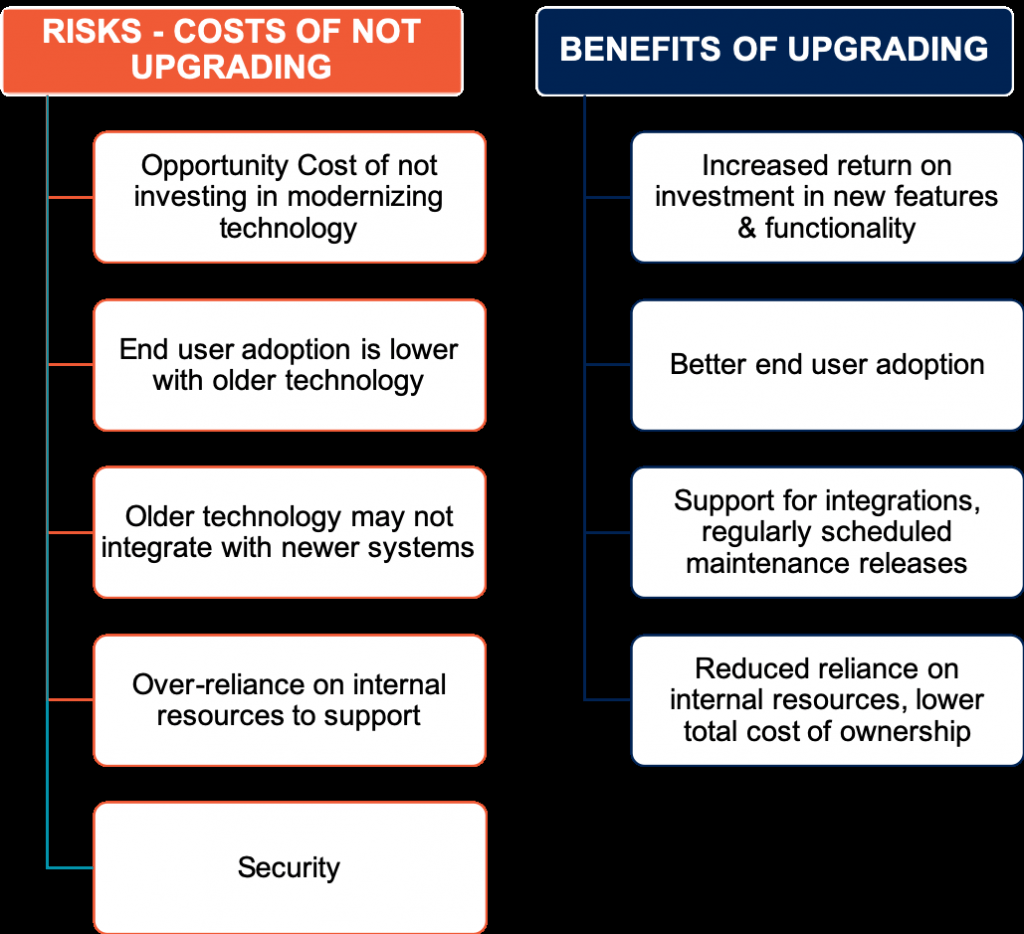
Updating your devices, software, and tools are mandatory. With time organizations and software, developers release patches and updates that improve not only the functionality but also reduce the risk of encountering security issues.
These updates are extremely important; otherwise, outdated technology becomes extremely vulnerable to attacks, and they can also be easily accessed by a hacker who is aware of loopholes and the lapse of security within the system.
10. VPNs
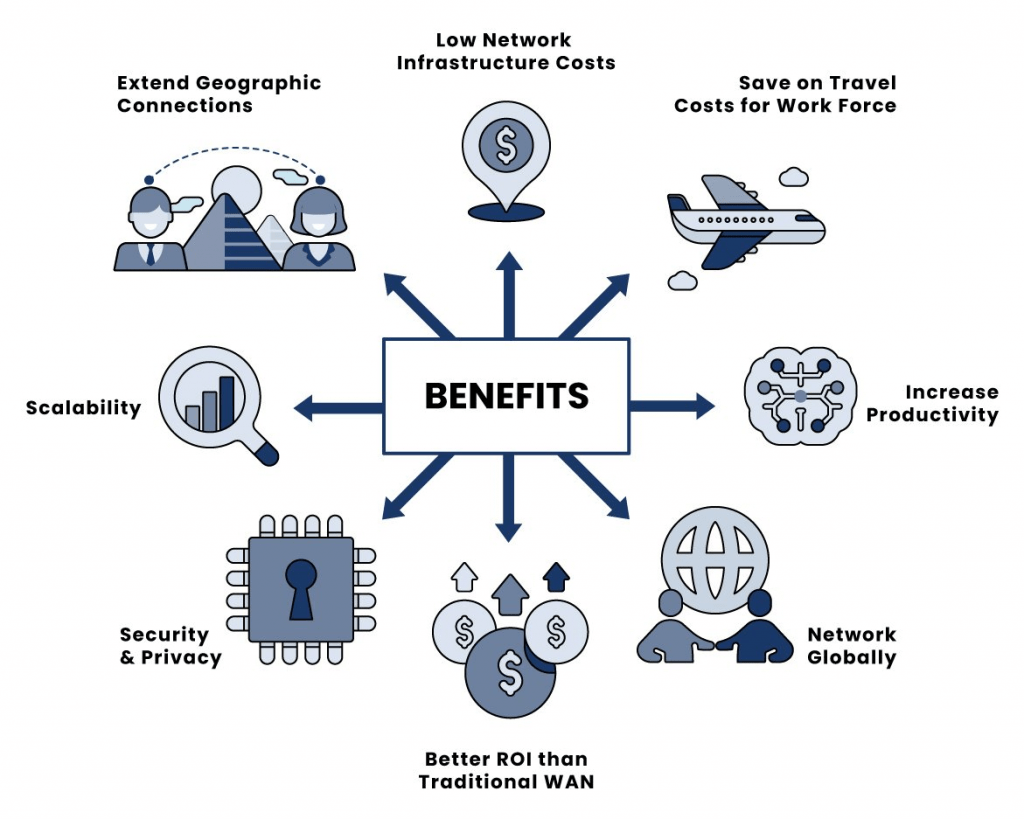
Using a VPN (a virtual private network) is also one of the methods that can add to your security when working with a remote team. VPNs offer you online anonymity and privacy through the creation of a private network from a public internet connection.
They also help in masking your IP (internet protocol) address, so when you go online, your actions become virtually untraceable.
Conclusion
Endpoint security is a crucial element to ensure the remote workers follow best practices. It can also be used to keep a check on their online activities and keep strict control over them to safeguard and protect volatile information and private data from being leaked out.
Through the aforementioned solutions, endpoint security can be used to protect information being lost or used by those with malicious intent. However, with the passage of time, cybercriminals are becoming increasingly innovative with their approach, which raises the concern to keep endpoint security features up to date.